
Identity and Access Management (IAM) Solutions
Identity and Access Management (IAM) is a framework of policies and technologies to ensure that the right users have the appropriate access to the right information technology resources. IAM is part of a bigger IT security and data management domain. Identity and access management systems mainly identify, authenticate and control access for individuals (employees, 3rd parties, partners, customers, contractors etc. ) who need to access to corporate IT resources.
We follow the principle of Zero Trust, "never trust, always verify,” which means that users and devices should not be trusted by default, even if they are connected to a permissioned network such as a corporate network and even if they were previously verified.
Process Requirements for Zero Trust
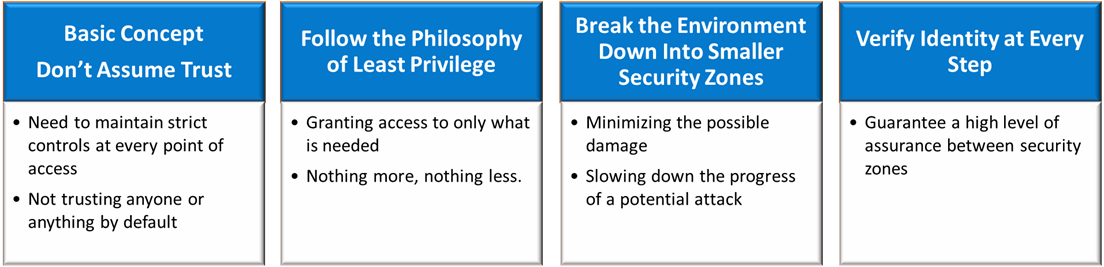
Required Building Blocks for Zero Trust

The zero-trust data security approach can protect access to the corporate data as it is more proactive than traditional approaches and probably the only way to combat sophisticated attacks.
A well designed and implemented Identity and Access Management is one of the pillars of Zero Trust concept.
Following form the identity foundation that can be built on;
- Identity Governance & Administration
- Access Management
- Privilege Identity Management
- Customer Identity & Access Management
- Data Security & Governance
- Multifactor Authentication
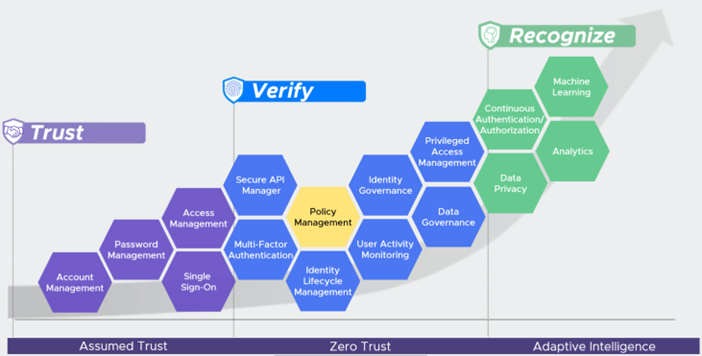
IAM basically covers Identity Management and Governance, Access Management, Privilege Management and Data Access Governance.
Identity Management & Governance
Our Identity Management and Governance solution basically addresses requirements such as; automated user provisioning and deprovisioning, role changes, self service password reset, active directory services, access request management and governance.
It helps organisations to automate user identity management to lower the security risks and improve operational efficiency by;
- Access Request
- Access Certification
- Worfkflow Orchestration
- Business Policy Management
- Self Registration / Activation
- dentity Life cycle
- Collection & Fulfilment
- Role Mining & Management
- User Profile Management
- Evidence & Compliance

Access Management
Access management basically provides access to complex environments supporting diverse services and situations that need customised user interaction. It provides a single environment to secure access for internal and cloud applications, using existing identity and roles. It will add multi-factor authentication as users attempt to access more sensitive data or areas of an application.
Following are the list of the functionalities provided by the Access Management;
- Access Enforcement
- Multi Factor Authentication
- Mobile Access
- Risk-Based, Adaptive Access
- Secure API Access
- Single Sign-On
- Federation
- Social Identity
- Password Management
Privilege Management
Most breaches involve gaining access to privileged credentials as they provide unlimited access to systems and data, creating a major security and compliance concern for;
- Managing privileged accounts
- Enforcing security control
- Overseeing privileged activity
- Reporting and auditing
With a well designed privilege management you could;
- Centralise credential management by enforcing consistent privileged access policies and controls.
- Enforce zero trust by flexible least privilege enforcement methods
- Improve security posture by risk-based access enforcement, analysis, and reporting
Privileged identities are found everywhere within an organisation and security standards are different in almost every circumstance – privileges can be found in applications, services, servers, databases, devices, things, etc. Most of the time there is also lack of insight into the users, dependencies and activity in privileged accounts. Often, privileges shared among multiple people, making it almost impossible for IT to hold anyone accountable for actions taken. Also, most are unable to extend their existing authentication or authorisation policies across platforms such as Linux or UNIX or to cloud services.
Following are the list of the functionalities provided by the Privilege Management;
- Privileged Access Management
- User Activity Monitoring
- Group Policy Management
- Secure API Access
- File Integrity Monitoring
- Change Monitoring
- Delegated Administration
- Audit&Compliance
- Admin Session Recording
Data Access Governance
The scope of Identity and Access Management (IAM) is evolving. Governing access to mission-critical data is imperative. Historically, the focus of data access was concentrated on application repositories associated with IAM systems. However, mission-critical data also lives as file-based, unstructured data. Unauthorised access of unstructured data is a risk that analysts, legislatures, CSOs, and compliance officers are all saying needs to be addressed.

Data Access Governance is all about the right people having the right access to the right data at the right time. When that doesn’t happen, one of two bad things occur. First, when the wrong people have access to key data, your organisation is at risk. Second, when the right people don’t have access to the data they need, the organisation is operating at less than efficient levels and people go out of band to share data, which can inherently put the data at risk.

If you aren’t effectively governing access to your data, you can’t meet the compliance requirements your organisation might be facing and you will have challenges fulfilling audit requests or attestation needs. In addition, you won’t be in a position to adapt to emerging and constantly evolving compliance requirements.
Technology Stack
Our technology stack comprises of following Opentext solutions. Each one of them covers specific areas of IAM requirements. They are totally modular, each module can be implemented independantly or they can be integrated to build a broader IAM solution.
- NetIQ Identity Governance
- NetIQ Identity Manager
- NetIQ eDirectory
- NetIQ LDAP Proxy
- NetIQ Access Manager
- NetIQ Advanced Authentication
- NetIQ Self-Service Password Reset
- NetIQ SecureLogin
- NetIQ Privileged Account Manager
- NetIQ Directory & Resource Administrator
- NetIQ Group Policy Administrator
- NetIQ Change Guardian
Top
