
Data Security Solutions
Encryption, Tokenisation and Hashing
The challenge in Data Security is mainly the volume of data, the sophistication of ubiquitous computing and the borderless flow of data are outpacing the ability to understand how personal data is being used. Our solutions enable organisations to manage risk, achieve regulatory compliance and capture the benefits of digital transformation without increased exposure to a breach of sensitive data.
Additionally global data privacy and protection legislations and regulations such as GDPR, KVKK, PCI/DSS, HIPAA also require the protection of financial, health and other personal data.
Format Preserving Encryption (FPE) is an effective method of protecting sensitive data. The data protection platform enables you to protect data over its entire lifecycle, from the point at which it’s captured, throughout its movement across your extended enterprise, all without exposing live information to high-risk, high-threat environments. That’s the essence of data-centric security. The data centric protection enables the protection of data at rest or while traveling between systems and platforms.
Following is an example of how we protect data using Format Preserving Encryption.
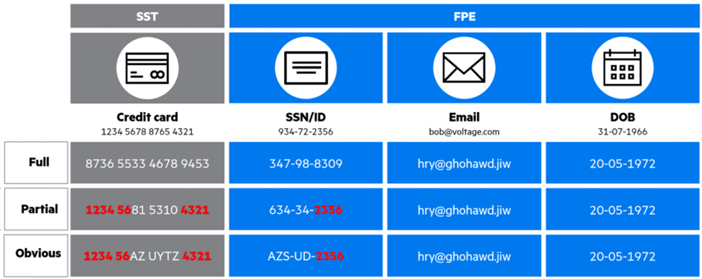
As described in the examples above, no modification is needed on the database column structure as the data is encrypted while keeping the format of it as is.
Alternatively tokenisation or hashing of the sensitive data can also be implemented according to the business requirements of the organisation.
Storing tokens instead of PANs is one alternative that can help to reduce the amount of cardholder data in the environment. When applied tokenisation dramatically reduces the number of PCI/DSS compliancy requirements.
While the tokenisation is reversible, Format Preserving Hashing (FPH) is irreversible making it a very good solution to obfuscate the data before transferring it to development or test environments. When hashed the data can then safely be used in the non-operational environments.
Dynamic Data Masking (DDM)
Dynamic data masking (DDM) by definition is a strategy for controlling or limiting unauthorised access to data, where data streams from a database or production environment are altered or “masked” as they are requested. Organisations may decide to dynamically mask the sensitive data before presenting it to the unauthorised users for many reasons.
We offer solution and services to address the DDM requirements. Our DDM solution can be deployed on premises and/or in the cloud. It communicates with ICAP (Internet Content Adaptation Protocol) capable network infrastructure, such as HTTP proxies and load balancers, to apply security policies to data traveling to and from the cloud, and it intercepts JDBC (Java Database Connectivity) and ODBC (Open Database Connectivity) API calls to apply security policies to data traveling to and from the database.
Key Benefits of DDM Solution
- Simplifies data protection for a wide range of applications without modification
- Accelerates time-to-value with flexible deployment of data security across hybrid IT
- Maintains centralised enterprise control over encryption keys and data in cloud services
- Promotes a non-disruptive approach to privacy compliance and the secure use of data
- Provides flexibility to choose from Voltage Format-Preserving Encryption, Secure Stateless Tokenisation, and Format-Preserving Hash protection methods at a field level
- Enables interoperability of encrypted data between multiple SaaS applications, independent of company size or geography
Key Functionalities of DDM Solution;
SaaS applications
- Data privacy broker functionality for transparent data protection in externally hosted cloud applications such as Salesforce, Microsoft Dynamics and ALM Octane.
COTS and in-house applications
- Data privacy broker functionality for transparent data protection of commercial off-the-shelf (COTS) applications and in-house enterprise applications.
Data Intercept
- Data intercept over key communication protocols, including ICAP/S, HTTP/S, and SMTP, and through popular APIs, including REST, SOAP, JDBC, and ODBC
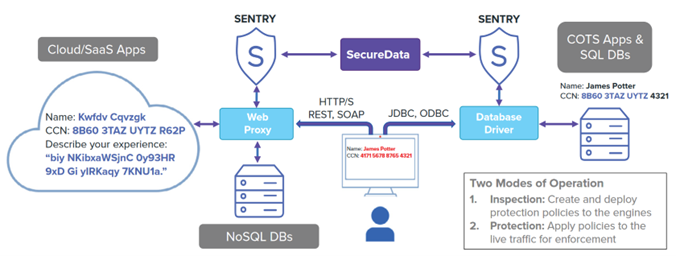
Technology Stack
Our technology stack comprises of following Opentext solutions. Each one of them covers specific areas of compliancy requirements. They are totally modular, each module can be implemented independantly or they can be integrated to build a broader data protection solution.
- Voltage SecureData
- Voltage Sentry
Top
