
Application Security Solutions
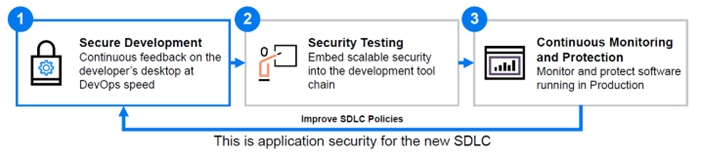
Application security is a combination of all tasks that are needed to ensure a secure software development life cycle for software development teams. It aims to enhance security practices by finding, fixing and finally preventing security vulnerabilities within applications.
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) analyses source code for security vulnerabilities in development phase. Compared to DAST, SAST can be utilised even before the application is compiled. As SAST has access to the full source code it is a white-box approach. This can yield more detailed results but can also result in false positives that can be avoided by optimisations.
Dynamic Application Testing (DAST)
Dynamic Application Security Testing (DAST) detects vulnerabilities generally by crawling websites. This method is highly scalable, easily integrated and quick yet it might impose negative effects on the website during the testing. The DAST tools can cover low-level attacks such as injection flaws but are not well suited to detect high-level flaws such as logical or business logic flaws.
Software Composition Analysis
Software development is more effective and faster by using different external components. They help avoiding rework and contributes to flexibility. The negative side of using external components is that they might also introduce following risks;
- Common Vulnerabilities & Exposures (CVEs)
- Legal Issues (Intellectual property rights)
- Additional risks by each new version
- Containers : Secure your containers by preventing vulnerabilities and misconfigurations from making it to production.
- Clients & Embedded : Build resilience into your Internet-of-things (IoT), connected devices and client apps with Fortify’s proven testing prowess.
Technology Stack
Our technology stack comprises of following Opentext solutions. Each one of them covers specific areas of IAM requirements. They are totally modular, each module can be implemented independently or they can be integrated to build a broader application security solution.
- Fortify SAST
- Fortify DAST
- Software Composition Analysis
